Why the future of APIs must include zero trust
hitesh nikam
API, APIs, Cyber, cyber security, cyberattacks, Cybersecurity, Cybersecurity attack, Data Security, DevOps, information, information technology, IT, IT security, Security, software, software development, technology, theinfotech
It’s the digital pandemic that no one talks about because it’s so difficult to quantify, prevent, and defeat the best cybersecurity defenses businesses have today. API attacks have increased by 681% over the past 12 months, compared to a 321% increase in total API traffic. Malicious API calls increased from a monthly average per customer of 2.73 million in December 2020 to 21.32 million in December 2021, according to the State of API Security Q1, 2022 report by Salt. Salt customers have web application firewalls, and almost all have API gateways and API attacks that bypass these controls.
The massive increase in API attacks is also stifling innovation. For example, 62% of companies admit to delaying new product launches and application deployments due to API security issues. Additionally, 95% of DevOps leaders and teams say they’ve experienced an API security issue in the past 12 months. One in three devops says they don’t have an API security policy, despite running APIs in production. According to Gartner, the proliferation of API breaches will accelerate and double by 2024. The number of API-related customer requests grew steadily from 2019 to 2021, with an average annual increase of 33%.
Getting API sprawl under control
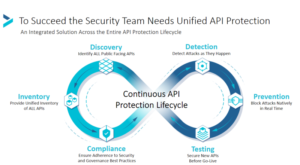
Devops leaders are pressured to deliver digital transformation projects on time and under budget while developing and refining APIs at the same time. Unfortunately, API management and security is an issue to consider as development teams rush to complete projects on time. As a result, the proliferation of APIs was rapid, multiplying when not all the company’s development teams had the APIs and security management tools they needed. More and more teams of devops need a solid and scalable methodology to limit the proliferation of APIs and give them the least privileged access. Additionally, DevOps teams need to move API management to a trustless framework to help reduce the growing number of breaches occurring today. The recent webinar sponsored by Cequence Security and Forrester, Six Stages Required for API Protection, hosted by Ameya Talwalkar, founder and CEO and guest speaker Sandy Carielli, Principal Analyst at Forrester, provide valuable insights into how devops teams can protect APIs. In addition, their discussion highlights how devops teams can improve API management and security.In the largest organizations, you’re dealing with hundreds of applications with APIs that expand and soon you’re dealing with tens of thousands or hundreds of thousands of APIs. So, the management and tracking of them become much harder and you still need all these different pieces to protect them.” Sandy Carielli, principal analyst at Forrester.Cequence Security’s approach to solving the challenges of API protection starts with Discovery or identifying all public-facing APIs first and progresses to inventory, compliance, detection, prevention, and detection.

I will tell you that when I first started getting calls about API security, you know what question number one almost always was, or problem number one always was was that discovery piece.” Sandy Carielli, principal analyst at Forrester.Inferred from the webinar is the need for APIs to be managed as the vulnerable, unprotected open threat surfaces they are. Cybercriminals know how unprotected APIs are, sending the attack rates into triple-digit growth rates. APIs need to be managed using a zero-trust framework.
API threat surfaces need zero trust
API breaches at Capital One, JustDial, Venmo, Panera Bread, T-Mobile, the United States Postal Service, and others illustrate that thousands of APIs are left unprotected and are one of cybercriminals’ favorite attack surfaces. APIs need the least privileged access and be managed using a more microsegmentation-based approach. These two elements of zero trust combined with an Identity and Access Management (IAM) framework to organize APIs will reduce the number of rogue and lost APIs all enterprises are having trouble tracking today. Additionally, applying least privilege, microsegmentation and IAM will reduce the number of endpoints used for internal tests left open that can access APIs.API lifecycles need to be built on zero trust
Security doesn’t need to be a constraint on devops anymore. Having zero trust engrained into API lifecycles starts by not trusting client-supplied data and having a default deny process to remove all implicit trust. Devops leaders need to build authentication into every phase of API lifecycles. The goal needs to be to design explicit trust into every API development and deployment project or initiative.Getting API governance right with zero trust
Devops leaders and their teams need help balancing their businesses’ ever-increasing needs for APIs to support new digital transformation projects versus the need to stay in compliance. Given the pressure to produce APIs so fast, devops teams accelerate business benefits first and attempt to catch up on compliance, security and privacy as development schedules allow. There must be a shift to API-level trust, with security context defined for each type of API produced.Strengthening CI/CD and SDLC with zero trust
Attacks on source code supply chains clarify that zero trust must be core to continuous integration/continuous delivery (CI/CD) and SDLC devops frameworks and processes. SolarWinds-level attacks that successfully change core executables of an application and then infect an entire supply chain are making zero trust an urgent issue for devops teams to deal with today. Security stops being a roadblock to getting code out when it’s designed into the SDLC. SDLC cycles would also run faster because security would cease to be a bolt-on process pushed to the end of a project, improving governance simultaneously.API security is too important to be a bolt-on
Devops team leaders rush through release cycles for their APIs to get large-scale digital transformation projects out, often seeing security as a roadblock to getting work done. Security checks and audits on APIs aren’t often finished, only completed at the cursory level. Everyone on the devops teams is pressured to meet or beat code release dates. API security becomes the bolt-on process no one has the time to deal with, contributing to API sprawl. When zero trust becomes a design goal for APIs and devops processes, security gets designed and strengthened throughout the SDLC. IAM and microsegmentation will drastically improve inventory accuracy, reducing the threat of rogue or forgotten APIs bringing an entire platform or company down with a cyberattack.See More

Faster Insights with Splunk AI Assistant for SPL: Now More Personal Than Ever
Splunk AI Assistant for SPL has revolutionized how users interact with Splunk’s powerful Search Processing Language (SPL), making data analysis more

From Complexity to Clarity: Leveraging AI to Simplify Fraud, Waste, and Abuse Investigations at Every Level
Fraud, waste, and abuse pose significant challenges across all sectors, from corporate enterprises to federal institutions. With increasing scrutiny from

Beyond the horizon: Navigating the bridge between today’s tech and tomorrow’s AI
On the calendar, a year has 365 days. But in the world of AI, it often feels like every month

Cyber Threats 2025: Dark Web Hacks, AI Malware, and Ransomware Take Center Stage
As cyber threats continue to evolve, 2025 marks a turning point for businesses and individuals facing increasingly sophisticated attacks. Hackers




